This describes how to setup a remote desktop gateway on a Server 2008 R2 machine which is not on a domain. Note that this is not a truely recommended structure as ideally the gateway should be on a separate server. But in the case of a hosted single server adding it all to the same server means that the traffic is encrypted over https and there is no requirement to have the terminal server port open on the external firewall – and so can provide an alternative if fixed IP addresses are problematic. Fixed IP addresses are still preferred as it adds additional security.
Make sure the required roles are installed:
http://technet.microsoft.com/en-us/library/ff519134(v=ws.10).aspx
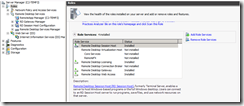
Decide how you are going to access this machine (e.g. no-ip or subdomain on esdm.co.uk – probably best). Set this up pointing at the machines external IP address. Its critical that the certifcate references this domain name (e.g test.esdm.co.uk in these screenshots)
Create a self signed certificate (or a proper one …)
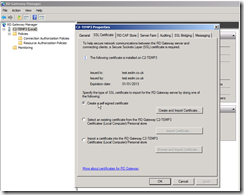
Create new user group and new users
In order to do this you will want to create a new user group (e.g. GatewayGroup)
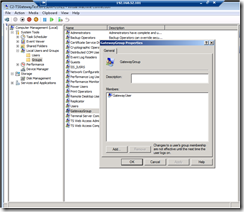
And then users for this group who are members of the required roles:
- Newly created group (e.g. GatewayGroup)
- Remote Desktop Users
- TS Web Access Computers
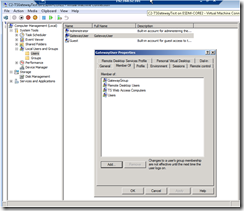
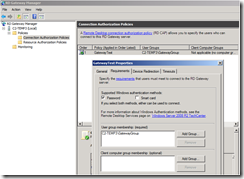
Create Connection Authorization Policy – CAP (at least one)
This basically controls who can access the gateway
Then assign newly created group to CAP
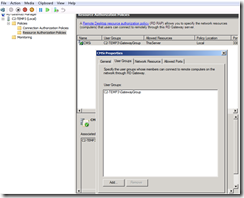
Create a Resource Allocation Policy (RAP)
This controls what a user that has authenticated on the gateway can access – normally controls what machines can be accessed etc – but in our case its only this one machine
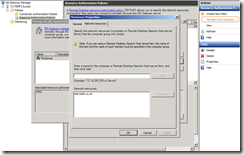
First we need to create a group of the machines we can access – in this case just the server itself. Click on the Manage Local Computer option on the right. The machine name seems to have to be the same as the domain name (e.g. test.esdm.co.uk) – calling it its local name or IP address didn’t work.
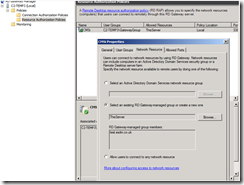
Then setup the RAP connecting the user group to the machine group
If using a generic published certificate - you may get connection warnings about:
"The remote computer could not be authenticated due to problems with its security certificate. It may be unsafe to proceed.
Name mismatch"
To fix this you need to (from http://support.microsoft.com/kb/2000960):
1. Open the "Terminal Services Configuration" windows in Windows Server 2008 or the "RD Session Host Configuration" in Windows Server 2008 R2.
2. Open the properties dialog of the "RDP-Tcp" connection.
3. On the "General" tab, check the selected certficate. Ensure that you select a correct certficate to make Terminal Server sessions or Remote Desktop sessions.
Once this is all done and you have applied – check that the Remote Desktop Gateway service is running and maybe restart it (I found after some changes it seemed to stop…)
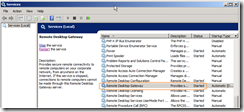
That should be it !
Then you need to test from a client.
Remember communication is now tunnelled through https – so you need port 443 open (which would normally be)
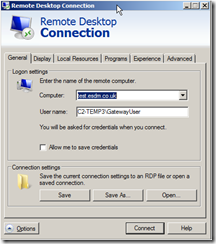
When setting up your connection:
- Make sure you use the domain name we have been using elsewhere (test.esdm.co.uk) – do NOT use an IP address or another name
- The Username – as we are not on a domain – should be machinename\username
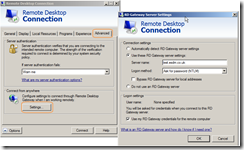
On the Advanced tab – select settings and setup the gateway – again making sure you use the same domain:
Before the connection will work – you must trust the certificate on the client machine – so copy the .cer file you created at the start onto the client machine and then:
Install this into the Trusted Root Certificate Store in Internet Explorer (instructions here for IE9):
Tools > Internet Options > Content tab > Certificates > Trusted Root Certification Authorities tab > Import... > Next > browse to the downloaded file, and complete the wizard.
You may get a couple of warnings when connecting (which you can opt to not be shown again). Probably wouldn’t get these with a proper certificate.